In this age of digital technology, many of us rely on email to conduct business – both personally and professionally, and there probably isn’t a day that goes by without checking our email accounts. With that convenience, comes a bit of risk. Email Compromise Fraud consists of schemes where criminals compromise a victim’s email account and send fraudulent wire transfer instructions to financial institutions. The two types of email compromise scams are Business Email Compromise (BEC) which target commercial customers and Email Account Compromise (EAC) which target consumer accounts.
How Do These Scams Work?
Both BEC & EAC schemes focus on using compromised email accounts to mislead banks and their customers to conduct unauthorized wire transfers. Both schemes can be broken down into three stages.
Stage 1: Compromising Victim Information and Email Accounts
Criminals gain access to a victim’s email account through social engineering or computer invasion techniques. The compromised email is then used to obtain information on the victim’s bank, account details, contacts and personal information.
Stage 2: Transmitting Fraudulent Transaction Instructions
Criminals use the victim’s stolen information to send fraudulent email instructions to the bank, making it appear as if it’s being sent by the victim. Criminals will either hack the victim’s email account (use their actual email address) or spoof their email account (create a fake email account resembling the victim’s email address).
Stage 3: Executing Unauthorized Transactions
Criminals trick the victim’s employee or bank in order to conduct unauthorized or fraudulent wire transfers. The wire instructions direct the funds to the criminals’ domestic or foreign bank accounts.
Business Email Compromise
Scammers primarily target banks, their commercial customers and municipalities. They target accounts that are used for pension funds, payroll accounts, and contracted services. These losses can impact government operations as well as government employees, citizens, and vendors. Criminals gain unlawful access to the email accounts of a company’s executive or employees to:
- Directly submit fraudulent transaction instructions to the company’s bank by impersonating company employees through emails and documentation related to the requested transfer.
- Mislead a company employee into submitting fraudulent transaction instructions to the company’s bank by impersonating a supplier or company executive to authorize or order payment through what appears to be legitimate internal emails.
Scenario 1: Criminal Impersonates a Financial Institution’s Business Customer
- Criminal hacks or spoofs an email account of a company’s employee to send fraudulent wire instructions to the company’s bank.
- The bank then issues the wire transfer and sends the money to a fraudulent account the criminal controls.

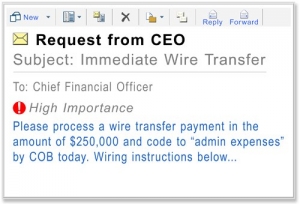
Scenario 2: Criminal Impersonates an Executive
- Criminal hacks into or spoofs an email account of an executive of a company.
- A fraudulent internal email is sent to a company employee to contact the bank to send a wire transfer.
- The employee who receives this fraudulent email is typically responsible for processing and issuing payments.
- The employee, believing the email is legitimate, orders the bank to execute the wire transfer. This is also known as Whaling.
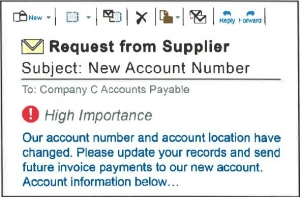
Scenario 3: Criminal Impersonates a Supplier
- Criminal impersonates a supplier of the company and sends a fraudulent email to the company to inform them future invoice payments should be sent to a new account number and location.
- The company updates its supplier’s payment information in their records and submits the new wire transfer instructions to its bank directing payments to the fraudulent account controlled by the criminals.
Email Account Compromise
- Unlike BEC, EAC targets individuals, not businesses. Common targets are individuals who conduct large transactions through banks, lending entities, real estate companies and law firms.
Scenario 1: Criminal hacks into the email account of a financial service provider like an accountant or broker. They email fraudulent instructions allegedly on behalf of a client, to the client’s bank or brokerage to wire funds to an account controlled by the criminal.
Scenario 2: The email account of a realtor or an individual purchasing or selling real estate is compromised. This is to alter payment instructions and divert the funds of a real estate transaction (i.e. sale proceeds, loan disbursements, fees). The criminal uses the realtor’s email address to contact an escrow company, instructing it to redirect commission proceeds to a fraudulent account controlled by the criminal.
Scenario 3: The criminal compromises an attorney’s email account to access client information. The criminal then emails fraudulent payment instructions to the attorney’s bank. Or the criminal will request wire transfers from the trust and escrow accounts the client’s attorney manages.
Red Flags for BEC & EAC Fraud
Suspicious Emails – Email contains different language, email signatures and amounts than what was previously discussed.
Timing of the Emails – If the email is hacked in a system such as Microsoft Outlook, the criminals can also access the calendar to see when the employee is in meetings or out of the office. Emails are delivered in a way that would give the bank limited time or opportunity to verify the transaction.
Unavailability – When the financial institution asks their customer to come into the branch to conduct the wire, they claim they are in a meeting or unable to get there – constantly not available.
Email Spoofing – The email address closely resembles the known customer’s email account, but it has been slightly altered by adding, changing or deleting one or more characters. (Example: john1doe at xyz dot com or John1doe@xzy.com)
Sense of Urgency – They ask to have the transaction completed by the end of the business day. Emails may be marked “urgent”, “confidential” or “secret”.
Be aware if you receive an email from a “customer” with any of the following instructions:
- Send a direct payment to a known beneficiary, but you see the account information is different from what was previously used.
- Direct the wire transfer or payment to a beneficiary the customer does not have a payment history with or documented business relationship. The amounts are also similar to past payment history or more.
- A wire transfer is received for credit into an account and names a beneficiary that is not the account holder of the record.
- The instructions are sent from a customer’s employee who is a newly authorized person on the account or who has not previously sent wire instructions.
- The customer email requests for additional payments immediately following a successful payment to an account not previously used by the customer to pay its vendors.
What to do if you are a victim:
- Contact the originating bank of the wire transfer and request the wire to be recalled.
- Immediately file a complaint with the FBI’s Internet Crime Complaint Center (IC3).
- Save all messages and evidence associated with the incident including:
- Victim's name, address, telephone, and email
- Financial transaction information (e.g., account information, transaction date and amount, who received the money)
- Subject's name, address, telephone, email, website, and IP address
- Specific details on how you were victimized
- Email header(s)
- Overall losses
- Any other relevant information you believe is necessary to support your complaint
Methods of Prevention:
- Contact requestors by phone before complying with email requests for payments or financial records.
- Monitor your email server frequently for changes in configuration and custom rules for specific accounts.
- Consider adding an email banner stating when an email comes from outside your organization so they are easily noticed, such as “EXTERNAL EMAIL ALERT” at the top of the email message.
- Ensure company policies provide for verification of any changes to existing invoices, bank deposit information, and contact information.
- Consider requiring two parties to sign off on payment transfers.
To learn more about other scams and how to avoid falling for them, check out our other blogs on Privacy & Cybersecurity and visit the Lakeland Bank identity theft information center. If you believe you have fallen victim to a scam or your personal information has been compromised, we’re here to help! Contact us at 866-224-1379.


